I received the following message today:
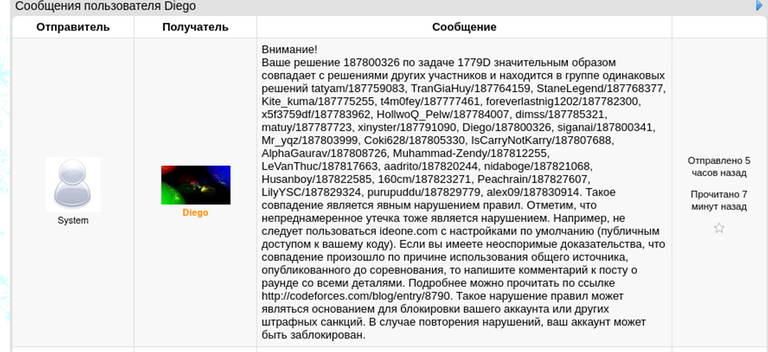
I only received the Russian version, the translation is below:
begin of translation
Warning.
Your solution 187800326 for Problem 1779D is significantly similar to the solutions of other participants and is in the group of the same solutions of tatyam/187759083, TranGiaHuy/187764159, StaneLegend/187768377, Kite_kuma/187775255, t4m0fey/187777461, foreverlastnig1202/187782300, x5f3759df/187783962, HollwoQ_Pelw/187784007, dimss/187785321, matuy/187787723, xinyster/187791090, Diego/187800326, siganai/187800341, Mr_yqz/187803999, Coki628/187805330, IsCarryNotKarry/187807688, AlphaGaurav/187808726, Muhammad-Zendy/187812255, LeVanThuc/187817663, aadrito/187820244, nidaboge/187821068, Husanboy/187822585, 160cm/187823271, Peachrain/187827607, LilyYSC/187829324, purupuddu/187829779, alex09/187830914. Such a match is a clear violation of the rules. Note that unintentional leakage is also a violation. For example, you should not use ideone.com with the default settings (public access to your code). If you have indisputable evidence that the match was due to using a common source published before the contest, write a comment on the roundup post with all the details. Read more at http://mirror.codeforces.com/blog/entry/8790. Such violation of the rules may be grounds for blocking your account or other penalties. In case of repeated violations, your account may be blocked.
end of translation
I just looked at most of the solutions mentioned. None of them use DSU like mine. Perhaps the overlap is due to my template, which contains SegTree in particular and some other useful features. However, this template was posted by me on github about a year ago: https://github.com/eropsergeev/cf-tempalte and the use of some parts from it by others is legal. Also, I was not able to recognize parts of my template in the solutions presented. Perhaps the system reacted to the large number of overlapping names like segtree?
In any case, the accusation of cheating is clearly unfounded.
MikeMirzayanov, can you please comment on this?









