C++ has always had the convenient data structures std::set and std::map, which are tree data structures whose operations take 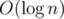 time. With C++11, we finally received a hash set and hash map in
time. With C++11, we finally received a hash set and hash map in std::unordered_set and std::unordered_map. Unfortunately, I've seen a lot of people on Codeforces get hacked or fail system tests when using these. In this post I'll explain how it's possible to break these data structures and what you can do in order to continue using your favorite hash maps without worrying about being hacked .
So how are they hackable? We always assume hash maps are O(1) per operation (insert, erase, access, etc.). But this depends on a key assumption, which is that each item only runs into O(1) collisions on average. If our input data is completely random, this is a reasonable assumption. But this is no longer a safe bet when the input isn't random, especially so if someone is adversarially designing inputs to our code (a.k.a. hacking phase). In particular, if they know our hash function, they can easily generate a large number of different inputs that all collide, thus causing an O(n2) blow-up.
We'll prove that now by blowing up unordered_map. In order to do that, we first have to determine exactly how it's implemented. For this we can dig into gcc's implementation on GitHub: https://github.com/gcc-mirror/gcc.
After some searching around we run into unordered_map.h. Inside the file we can quickly see that unordered_map makes use of __detail::_Mod_range_hashing and __detail::_Prime_rehash_policy. From this we can guess that the map first hashes the input value and then mods by a prime number, and the result is used as the appropriate position in the hash table.
Some further searching for _Prime_rehash_policy leads us to hashtable_c++0x.cc. Here we can see that there is an array called __prime_list, and the hash table has a policy to resize itself when it gets too large. So we just need to find this list of primes.
The one include on this file leads us to hashtable-aux.cc. Aha, here is the list we're looking for.
One more thing: we need to know the hash function unordered_map uses before modding by these primes. It turns out to be quite simple: the map uses std::hash, which for integers is simply the identity function. Armed with this knowledge, we can insert lots of multiples of one of these primes to the map in order to get n2 blow-up. Not all of the primes work though, due to the resizing policy of the map; in order for a prime to work, we need the map to actually resize to this prime at some point in its set of operations. It turns out the right prime depends on the compiler version: for gcc 6 or earlier, 126271 does the job, and for gcc 7 or later, 107897 will work. Run the code below in Custom Invocation and see what output you get.
#include <ctime>
#include <iostream>
#include <unordered_map>
using namespace std;
const int N = 2e5;
void insert_numbers(long long x) {
clock_t begin = clock();
unordered_map<long long, int> numbers;
for (int i = 1; i <= N; i++)
numbers[i * x] = i;
long long sum = 0;
for (auto &entry : numbers)
sum += (entry.first / x) * entry.second;
printf("x = %lld: %.3lf seconds, sum = %lld\n", x, (double) (clock() - begin) / CLOCKS_PER_SEC, sum);
}
int main() {
insert_numbers(107897);
insert_numbers(126271);
}
Depending on which compiler version you are using, one of these two numbers will take much longer than the other. There are several other primes that also work; try some more for yourself!
Note that for other hash tables like cc_hash_table or gp_hash_table (see Chilli's helpful post), it's even easier to hack them. These hash tables use a modulo power of two policy, so in order to make a lot of collisions occur we can simply insert a lot of numbers that are equivalent, say, modulo 216.
Don't want to be hacked?
Let's look at how to safeguard these hash maps from collision attacks. To do this we can write our own custom hash function which we give to the unordered_map (or gp_hash_table, etc.). The standard hash function looks something like this:
struct custom_hash {
size_t operator()(uint64_t x) const {
return x;
}
};
However as we mentioned, any predictable / deterministic hash function can be reverse-engineered to produce a large number of collisions, so the first thing we should do is add some non-determinism (via high-precision clock) to make it more difficult to hack:
struct custom_hash {
size_t operator()(uint64_t x) const {
static const uint64_t FIXED_RANDOM = chrono::steady_clock::now().time_since_epoch().count();
return x + FIXED_RANDOM;
}
};
See my post on making randomized solutions unhackable for more details. Awesome, so our hash is perfectly safe now, right? Not so fast. All we've done is add the same fixed number to every input to the function. But if two numbers a and b satisfy a = b (mod m), then a + x = b + x (mod m) for every x as well. Similar problems occur for other very simple hash functions: multiplying by a random large odd number (and overflowing mod 264) is likely effectively modulo p, but will be problematic for gp_hash_table's power of two policy; the same situation occurs for xor-ing with a random number.
A slightly better hash function like the following may look enticing:
struct custom_hash {
size_t operator()(uint64_t x) const {
static const uint64_t FIXED_RANDOM = chrono::steady_clock::now().time_since_epoch().count();
x ^= FIXED_RANDOM;
return x ^ (x >> 16);
}
};
However, if you are using a gp_hash_table this actually still leaves you susceptible to hacks from a strong enough adversary. In particular, after inserting the numbers (1 << 16) + 1, (2 << 16) + 2, (3 << 16) + 3, ..., into this hash table, all of the outputs will be equivalent modulo 216. (Do you see why?)
So we want a better hash function, ideally one where changing any input bit results in a 50-50 chance to change any output bit. Note for example that in the hash function x + FIXED_RANDOM, this property is not satisfied at all; for example, changing a higher bit in x results in a 0% chance of changing a lower bit of the output.
Personally, I like to use splitmix64, which is extremely high-quality and fast; credit goes to Sebastiano Vigna for designing it. Adding all this together, we have our safe custom hash function:
struct custom_hash {
static uint64_t splitmix64(uint64_t x) {
// http://xorshift.di.unimi.it/splitmix64.c
x += 0x9e3779b97f4a7c15;
x = (x ^ (x >> 30)) * 0xbf58476d1ce4e5b9;
x = (x ^ (x >> 27)) * 0x94d049bb133111eb;
return x ^ (x >> 31);
}
size_t operator()(uint64_t x) const {
static const uint64_t FIXED_RANDOM = chrono::steady_clock::now().time_since_epoch().count();
return splitmix64(x + FIXED_RANDOM);
}
};
Now we can simply define our unordered_map or our gp_hash_table as follows:
unordered_map<long long, int, custom_hash> safe_map;
gp_hash_table<long long, int, custom_hash> safe_hash_table;
Once we use these in our program above, it runs very quickly:
x = 107897: 0.035 seconds, sum = 2666686666700000
x = 126271: 0.031 seconds, sum = 2666686666700000
=====
Used: 109 ms, 9204 KB











Added to my snippets ;). Amazing Work.
c++ 17 when set with same key has size larger than 8 it will use RBT to store data.
Are you saying
unordered_settransitions to using red-black tree when it encounters 8 collisions in the same location? This isn't true. In the code snippet I posted above,insert_numbers(107897)in G++17 takes about as long asinsert_numbers(126271)in G++14.Oh, i am wrong,it was implemented in jdk1.8.
Do you have a link to where it says this? I'm interested in reading the documentation for it.
http://hg.openjdk.java.net/jdk8/jdk8/jdk/file/tip/src/share/classes/java/util/HashMap.java
do tell me some computer science books to read.Especially ones that have bizzare concepts and algorithms.
PS: Big Fan and already have CLRS, CP handbook etc. Also i need help cause i am not from Computer Science Background.
Yes very useful blog
But how did you use emoji?
How convenient! Thanks a lot!
very cool. keep it up!
Cool! I'm curious how many people actually do anti-hashing hacks in contest. Could you put the standard unordered_map runtimes on the inputs to use as comparisons to the benchmarks you put at the end? Or does it simply take way too much time to even record?
The thing about this specific hack is that if anyone successfully makes this hack on anyone else in the contest, their test will be added to system tests which will leave you in trouble. A few examples of recent problems where you can fail for using unprotected
unordered_mapinclude 1027F - Session in BSU and 1039C - Network Safety.As far as runtime, it gets a bit slower with the custom hash but not too much. Pure
unordered_mapgives anywhere between 0.00s and 0.04s on non-adversarial cases when running with Custom Invocation, vs. 0.03s with custom hash. If you're concerned with speed thengp_hash_tablewith the custom hash is the way to go, since it uses power of two modding and linear probing rather than prime modding and collision chaining.Oh, I wasn't that concerned about the speed of your custom hash. I was curious about the speed of
std::unordered_mapon the adversarial case that you've created. However, reading it more closely, you have N = 105, so if it really is causing an O(n2) blowup onstd::unordered_map, then it's probably too slow to bother recording the time.Ah. Run the code from the post in Custom Invocation :)
More than $$$169$$$ seconds on G++23 with prime $$$85229$$$
I like
(uintptr_t)main. :) This pointer should be random for every run because of OS security issue.Interesting idea. Unfortunately when I tried it on Codeforces just now, it gave the same result every time. :(
Really!? That's too sad. T_T It worked for most other OJ platforms...
You may try
new charNicely written, as always. Thanks!
Whenever someone talks about hacking hashmaps, I think of this problem: https://ipsc.ksp.sk/2014/real/problems/h.html
Thanks for this helpful blog. For completeness, it should be noted that the last definition
gp_hash_table<long long, int, custom_hash> safe_hash_table;should be preceded by
The following is a slight update to your test program.
Update
How does it compare with alternating max_load_factor of the hash table? because it is runs slower as compared to this trick (Arpa's Blog):
this gives output of:
This doesn't make it unhackable, it just changes the prime number that breaks it. Try calling
insert_numbers(1056323);instead:I am not sure I understand how it "only" changes the prime number because according to the code, you are inserting numbers with same modulo wrt the prime. Running on equal modulo numbers with:
which gives output of:
Also
reservemust change according to the elements to be inserted (upper bound to be a power of two). Maybe it's because of rehash scheme whenmax_load_factoris achieved in the bucket under consideration.When you call
.reserve()you are changing the internal capacity of the map, which means you are effectively changing the internal prime number modulo it uses out of this list.So yes if you change the capacity again, it will work well on the previous prime number I gave you, but there will be a new number in the list that is problematic.
How do you find the prime number from the list which will be able to cause a blowup?
The list (https://github.com/gcc-mirror/gcc/blob/master/libstdc%2B%2B-v3/src/shared/hashtable-aux.cc) mentioned above doesn't contain too many numbers in fact. We can just write a program and test which one will lead up to a blowup.
What if i need unordered_map<pair<int,int> , int> mp; here first is pair . What if more complex such as use (1,2,3,4) as first , i meant for struct data type first .
Read the comment right below this one. https://mirror.codeforces.com/blog/entry/62393?#comment-464775
are you too lazy, to copy comment?
are you too lazy, to click link?
like
splitmix64is there a good hash function for pairs too?If you have a pair of integers you'd like to hash, you can use the custom hash function above on each of them to get two values
aandb. Then combine them in any way you like, e.g.,a + b.The one issue with
a + bis that swapping the two elements of the pair will lead to the same hash value. This isn't a problem from a theory point of view since "O(1) collisions on average" is still valid, but to avoid this situation you can switch to a non-symmetric function such as3 * a + bora ^ (b >> 1).And how would you go about using unordered_set with strings as keys?
Here is an idea to use a random seed in the MurmurHashUnaligned2 which is the hash function that C++ uses by default for hashing strings: https://stackoverflow.com/a/34976823/10017885 although here it is written that even with using a randomized seed MurmurHash can be hacked: https://en.wikipedia.org/wiki/MurmurHash#Vulnerabilities
sha256(constant random string + desired string) --> never hacked again
But I doubt anyone would care enough to hack your murmurhash solution, if you ever used it.
And what fuction would you recommend for hashing ints?
Read the post.
In your post you provide a function for hashing long longs and I am interested in a good function for hashing ints.
Well, I suppose the same function would also work but maybe for ints we could have a function that is faster and also works.
Using the idea in neal's comment
Thanks for this blog, neal. Can you recommend a fast hash function that is not difficult to remember (for
gp_hash_table)?Can
xorshift64be such function?Next code:
returns
cnt = 4095.UPD2. I got idea about calculation polinomial hash from s, where
x = s[0]+(s[1]<<16)+(s[2]<<32)+(s[3]<<48). Tested it and it is fast.very helpful !!
you write very good and you need just another blog like this one to be in "Top contributors List".
neal Why use size_t as the return value of operator(), why not int64_t, does it affect the performance of functions
Why does this code take more than 2 seconds in custom invocation with C++17, while the same code with the 1e6 replaced by 1e9 takes less than 100 ms?(also, replacing 1e6 by 1e5 makes the running time over 10 seconds)
Good question. This is actually quite tricky. It's because the default hash function returns a
size_t, and on Codeforcessize_tis a 32-bit integer. This means that multiplying by an integer up to 1e9 actually overflows 32 bits when hashed and ends up with a number that is no longer a multiple of our prime.I didn't get it. So if I have an array like [1,1,1,1......,1], your hash function is not deterministic because hash(1) != hash(1) because it uses some FIXED_RANDOM. If the FIXED_RANDOM would be the same for all numbers, then I think we are the begining. Correct me if I am wrong. Thanks.
Just wanted to ask this, that for largest value possible in long long int x, this x += 0x9e3779b97f4a7c15 expression will overflow bounds of uint64.
Also the argument for hash requires unsigned int64 value, but if we have negative numbers to hash too, then what happens.
Thanks.
Thanks a lot for this post! It was in detail and very useful..
Absolutely beautiful!
Hey Nice Blog, But I have a doubt.... I have submitted same code(both have your custom_hash).
Problem : Social Network
My Solutions : unordered_map , unordered_set
I have a doubt that, i am getting TLE while using custom_hash with unordered set, but got ac while using same custom hash in unordered map. is there any reason for this? does your custom hash works faster on map than set or anything else?
It's not the custom hash. Your
existfunction passes the entire set by value instead of by reference.Got it !! And sorry for asking wrong question.
btw, thanks got ac by making it refernce.
Can you please send the improved code?
means??
Can we use this custom hash in unordered set as well??
yes, u can see my code.
Can u please give link to your code
Using map<vector,int> mp; gives me TLE.
I want to use Unordered_map to avoid TLE.
How can i make it? Any help is appreciated. Thanks.
Question : 1225D - Power Products
My Submission : 77023902
neal Please help
The complexity of your program with map<vector,int> is $$$O(n^2)$$$, assuming that $$$a_i \leq n$$$. Using an unordered_map will just remove a log factor, try improving your complexity by more than that.
size_t is 32 bit in 32 bit compilers. Is using 64 bit hash function splitmix64 good then? Or do you know any better hash function for 32 bit?
I think this comment on stack overflow is quite great.
https://stackoverflow.com/a/12996028/4275047
I'm getting this weird compiler warning on macOS when I make a basic unordered_map<ll,int,custom_hash>:
These are my compiler flags
Does this custom hash increases running time because i used this custom hash in a problem and it got Time Limit Exceeded as verdict and without custom hash function it got accepted Link to Accepted solution and Link to TLE solution .
neal or somebody please help...
We always assume hash maps are O(1) per operation (insert, erase, access, etc.). But this depends on a key assumption, which is that each item only runs into O(1) collisions on average. If our input data is completely random, this is a reasonable assumption. But this is no longer a safe bet when the input isn't random, especially so if someone is adversarially designing inputs to our codeSo if the input is random, custom hash will be worse.
Tried submitting your exact AC solution but it gives TLE now. Also still TLE for custom hash. Probably codechef updated their testcase.
i tried using the above hash function for this quesn — https://www.codechef.com/LRNDSA10/problems/MATTEG
but i still get TLE
my solution — https://www.codechef.com/submit/complete/37329776
what am i doing wrong?
Hi I have tried to change (unordered_)map to many thing like this ones but every time I get TLE on last testcase; I think this idea should be change but if anybody can help me, I ll be happy. link of submission
Your article is very helpful for me. I want to share this article to other Japanese, so I translated it to Japanese. 日本語訳(Japanese): https://qiita.com/recuraki/items/652f97f5330fde231ddb
I ran into this problem while upsolving. Turns out that test case 31 problem F from round 701 was specifically designed to blow up unordered maps. Quite nasty to do that but at least I learnt something. I'm glad I found your post because I had no idea what was going on.
Can unordered set collation cause wrong answer ? If anyone know plz reply.
Bump because of recent contest hacks on problem C for this reason.
Bump
deleted
Absolutely perfect! I wanted to increase my knowledge upon this matter and understand what is going underneath the hood explaining the so much hacks we've seen in recent contests for UNORDERED hash map. I think it is not safe at all to use that unordered version.. This blog is bumpped by hacks every now and then lol
My submission for 1561D1 - Up the Strip (simplified version) is getting TLEed using your custom hash!
Submission : 164724313
Have you considered the possibility that your algorithm might be garbage?
When runtime is important, don't use a hash map unless you absolutely have to. It's one of the slowest O(1) algorithms.
Your solution gets TLE even with normal map
Without using custom_hash :
using custom_hash. :
:using c++ 17.
why time is not decreasing ? neal
It depends on your specific compiler version. Try some other primes from the list above until you figure out which one is bad for yours in particular
TLE solution with your custom hash : 2206 ms
AC solution with normal map : 118 ms
Why?Can you please clarify why this had happened?
I think
.clear()is very slow for hash maps in generalI also thought that but don't know why it is technically very slow ,can you please come up with details what are the technical reasons .clear() is slow if you have time someday?
It's due to a bug on GCC,
clear()works in a time complexity of $$$O(\mathbf{capacity})$$$. However, due to the bug,clear()does not clear the capacity (i.e. "deallocate") after clearing, therefore the repeated use of the function takes a massive amount of time.this bug is in every version of gcc or just in gcc 9.2.1 of atcoder?
The bug still exists in the latest version (at least up to GCC 11, from what I know) on major Online Judges.
Why always using these cryptic hashfunctions with XORs and Shift operations?
Carter-Wegman should do the job perfectly fine, right? https://en.wikipedia.org/wiki/Universal_hashing#Hashing_integers
This looks like it'll probably work fine, but a few reasons that come to mind:
splitmix64as mentioned above is a perfect bijective mapping from $$$[0, 2^{64})$$$ onto itself; what you wrote above compresses 64-bit numbers into 31-bit numbers which may not be idealregarding mod: It seems like mod p with p being a Mersenne prime is actually pretty cheap because it can be implemented with bitshifts and addition (See: https://en.wikipedia.org/wiki/Lehmer_random_number_generator#Implementation and https://sortingsearching.com/2020/05/21/hashing.html) Tomek Czajka (the second link) even says that good compilers do that automatically.
regarding the mapping: Yeah thats probably something this can't do. There are other Mersenne Primes (https://oeis.org/A000043) and $$$2^{61} - 1$$$ seems to be the greatest below $$$2^{64}$$$. Thus the interval can be expanded. But surely its no bijection.
So, ... thanks for pointing out the advantages ;)
For some reason, $$$107897$$$ and $$$126271$$$ no longer seem to result in an $$$n^2$$$ blow-up on C++ 20.
I'm not sure exactly why this is the case, since they worked almost a year ago when I made the tests for https://mirror.codeforces.com/contest/1748/problem/C.
This solution used to get TLE, but now passes only on C++ 20.
I have tried several other primes from hashtable-aux.cc and none of them seem to work. neal
That's not too surprising on a new compiler version. Some of the primes should still work though. Keep trying more!
For GNU G++20 13.2 (64-bit, winlibs), the best candidates are $$$85229$$$, $$$172933$$$ and $$$351061$$$.
Use $$$85229$$$ for C++23. This should work for C++ 20 also
Hi Neal! Thank you a lot for the post! Why I don't see any improvements with your hash? I am using the g++ -std=c++20
Without your hash
And with your hash
On average, they look similar and I didn't see the performance difference as it was described in the post. Why?
The hash decreases the probability of an O(n^2) blowup, it doesn't change the complexity or commit to some improvement in the other cases, so...
Based on my recent tests, using $$$172933$$$ and $$$85229$$$ with
g++ -std=c++20version yields better results. In fact, for different g++ versions, you need to find different numbers, as neal mentioned. You can test within the prime number table to find them.Is there any particular reason to use
splitmix64(x + FIXED_RANDOM)instead ofsplitmix64(x ^ FIXED_RANDOM)which is a little bit faster?I think this issue should be patched by Codeforces just like I/O are patched because it's completely technical. I believe many people not using a template (including me) know this one but don't want to implement randomized hashing during the contest because it's just too complicated. (Also this post was posted 5 years ago but no one seemed to give this suggestion)
MikeMirzayanov
IO is not patched by CF??? If you do not use fast IO, you will tle on quite a few problems.
Just use map, its fast enough in 99% cases (umap isnt much faster than map given its high constant)
was it patched recently ?
Beautifully Explained!! I was doing a porblem on CSES by using sliding window where I got TLE while using unordered_map and then it passed using map, that is how i discovered collisions for the first time:
with unordered_map : CSES Playlist with unordered map
with map : CSES Playlist with map
Do i have to import something to use hash set error = "identifier "gp_hash_table" is undefined"?? Iam new to all this.. gp_hash_table<long long, int, custom_hash> safe_hash_table;
It shows compilation error in codeforces. Works fine on my machine.
Not sure what was up with your machine, but you missed the header
<chrono>, hence the CE log:program.cpp:35:51: error: 'std::chrono' has not been declared.Either uncomment your
bits/stdc++.hdeclaration, or#include <chrono>.i got tle with unordereedmap with custom hash https://mirror.codeforces.com/contest/1778/submission/264624245
and AC
With vector
https://mirror.codeforces.com/contest/1778/submission/264626174
so it s not safe always
you have to understand the fact that your first step is to see whether solution is possible without map then if you see it's not possible without map then it's a question of choosing ordered/unordered.So comparing safety between vector and unordered map is pointless
is there is way to make sur unordered map with chash is o(1) ?
unordered map in on average $$$O(1)$$$ with custom hash and vector operations is obviously constant $$$O(1)$$$ , so it's little faster than unordered map obviously , your vector solution almost TLEed too(almost 1800 ms),unordered map here didn't act much slower , it's good enough , it's just your solution isn't too good
Is it applicable to Python dictionaries? Meaning can we use the same hash function within the
intwrapper class?I stumbled upon this blog post: Anti-hash-table test in Python and thought if the solution proposed there is sufficient and secure against the stronger adversaries, like mentioned in this post.
Useful
Thanks for the helpful blog. This is really convenient. I recently got hacked for the same reason on using an unordered map. Will implement this next time onwards
If I had read this blog couple of days ago, my solution in the last contest won't get hacked. I used C++23.
When I ran the above snippet to test time. This is what I got. I am literally shocked.
The prime for C++23 is $$$85229$$$.
Just to see the difference, if you use the same code for
map, this is what you'll get on average:Thanks for this awesome helpful blog <3
How can I write the hashing function if I need this in a physical contest (e.g. IOI)? Because memorizing the function is nearly impossible. I am asking solution Only for
unordered_map, cause I don't usegp_hash_table.Question link
Using unordered map with custom hash mentioned above for storing frquency/kind of prefix sum but gives TLE and using map gets accepted.
For the first time I have seen unordered map with this custom hash is getting TLE because of it.
Can anyone please explain it