UPD: The RCPC token wall seems to have been removed. As of the time of this update, no additional security check is needed to access codeforces. Hence this script has been rendered obsolete by this change, and you will receive an error message if you attempt to run it.
As a result of a recent security update, many codeforces tools have been broken. In short, in order to access codeforces, a token is now required, which is decoded by the browser through a javascript implementation of AES. I have explained the specifics of this in my previous blog: https://mirror.codeforces.com/blog/entry/80070.
The token is different based on your IP address, and must be sent as a cookie with all requests to codeforces. Failing to do so will result in codeforces responding with a redirect page, containing the encrypted cipher token.
I have written an ad hoc script to decode this token using python.
https://github.com/great-prophet/adhoc_cf_rcpc_token_decoder
This script makes a request to codeforces to get the raw response with the AES cipher parameters, parses out the encrypted cipher, decodes it using an equivalent python AES implementation, and returns a hex formatted token. To use, simply run "source/cf_rcpc_token_decode.py" without input, with a python 3 interpreter.
Here is a screenshot of the expected behavior:
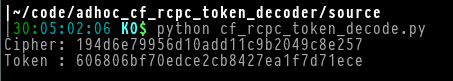
Note: You can ignore the "Cipher" output. It is the raw encrypted token, before decoding.
This token should be passed as a cookie with the key "RCPC" in all codeforces requests. For example, here is how you would do so with curl:
curl 'https://mirror.codeforces.com' -H 'Cookie: RCPC=606806bf70edce2cb8427ea1f7d71ece'
This script, by itself, will not automatically fix broken cf tools. You will need to have some technical knowledge in order to manually add the cookie as described above. This process is different for every tool. However I hope it can serve as a foundation for implementing a general fix.
Disclaimer: My current script is very very hacky and may be broken by future changes. However I will try my best to maintain it if an update does occur.










Thanks ! My submission tool works now, i just need to pass the RCPC as a cookie while making the request
Here is the python sample
Is this fix permanent btw?
Nice! I'm very happy to hear that my tool is working.
I created this tool from open source data I've been able to gather as explained in my previous blog. As such, unfortunately I can not guarantee that this tool we remain functional if there are any new changes. Currently your guess is as good as mine as to when codeforces will update this system again.
I will try to maintain this tool to the best of my abilities if an update does occur.
As I understood, "SlowAES" is just AES.
gave me the same result
I believe that is worst "proof-of-work" could be invented. It relies on "security-by-obscurity", but does not guarantee that attacker will spend enough time on every request without attribution.
Usual "proof-of-work" scheme on CTFs: provide answer to question like "hash(salt + x)[:6] = 'abc012'". While we concerned to make proof-of-work not burdensome for mobile users and still heavy for attacker with GPU, I propose Argon2 as hash, tuned by #iterations for sub-1ms time for server and prefix for ~1s for mobile user. Salt is against pre-calc. Change cookie with (IP, day) pair looks resonable.
CF tools could obtain token for passing in cookies by external program (for example on Python).
Thank you for your comment. Your implementation is much more elegant than mine. Do you if I use it to update mine?
As a side note: My initial guess was also that "slow" referred to some sort of "proof-of-work" system. However I have later found that this code comes from: https://code.google.com/archive/p/slowaes/
In actuality, from what I understand "slow" just refers to how it is implemented for interpreted languages (and is hence unintentional). I am still not completely sure what this "security feature" on codeforces is suppose to accomplish.
Yes, you can.
I assumed that there is nginx module for such anti-DDoS and there is — test_cookie with the same "SlowAES" scheme :) Looks like it is not proof-of-work, but just mitigation against stupid generic bots, which do not even use headless browser.
satoshi: invents bitcoin
11 years later:
Miner rode across the river
The miner sees — in the river the miner
Put miner miner into miner
Miner miner miner miner
It seems that CF added RCPC cookie again. Thanks a lot for your tool, it saved me from pain!
Is it still working? As of now I'm getting this error: